Настройка Apache с Let’s Encrypt сертификатом на CentOS 7 / 8
Продолжаю делать шпаргалки по настройке web-сервера. Инструкция по установке LAMP находится здесь.
Документация по certbot расположена здесь.
Открываем порты
|
1 |
iptables -I INPUT -p tcp --dport 443 -j ACCEPT |
Установка certbot
Для CentOS 7
|
1 |
yum -y install epel-release mod_ssl python-certbot-apache |
Для CentOS 8
|
1 |
dnf install epel-release certbot python3-certbot-apache mod_ssl |
Далее настраиваем certbot. Для CentOS версий 7 и 8 далее код не отличается. Ключ —apache значит, что скрипт автоматически настроит apache сервер. Здесь и далее example.com меняем на свой домен, admin@email.com — на свой email.
|
1 |
certbot --apache -m admin@email.com -d example.com -d www.example.com |
В процессе установки появится сообщение
|
1 2 3 4 5 6 7 |
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v02.api.letsencrypt.org/directory - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (A)gree/(C)ancel: |
Вводим A, чтоб согласиться c условиями.
|
1 2 3 4 5 6 7 |
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: |
Вводим N, чтоб не получать спам на почту.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
IMPORTANT NOTES: - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration. |
1 — без переадресаций
2 — с http переадресация на https
Успешная установка заканчивается фразой:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/example.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/example.com/privkey.pem Your cert will expire on 2019-03-05. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - Some rewrite rules copied from /etc/httpd/conf/httpd.conf were disabled in the vhost for your HTTPS site located at /etc/httpd/conf/httpd-le-ssl.conf because they have the potential to create redirection loops. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le |
Если в процессе установки возникла ошибка:
|
1 |
Unable to find a virtual host listening on port 80 which is currently needed for Certbot to prove to the CA that you control your domain. Please add a virtual host for port 80. |
Необходимо в конфиге apache /etc/httpd/conf.d/vhosts.conf (если файла нет, его нужно создать) добавить виртуальный хост на 80 порт:
|
1 |
vi /etc/httpd/conf.d/vhosts.conf |
|
1 2 3 4 5 6 |
<VirtualHost *:80> ServerAdmin admin@email.com ServerName example.com ServerAlias www.example.com DocumentRoot /var/www/html </VirtualHost> |
Сохраняем файл, перезапускаем сервер, выполняем пункт с настройкой certbot заново.
|
1 |
systemctl restart httpd.service |
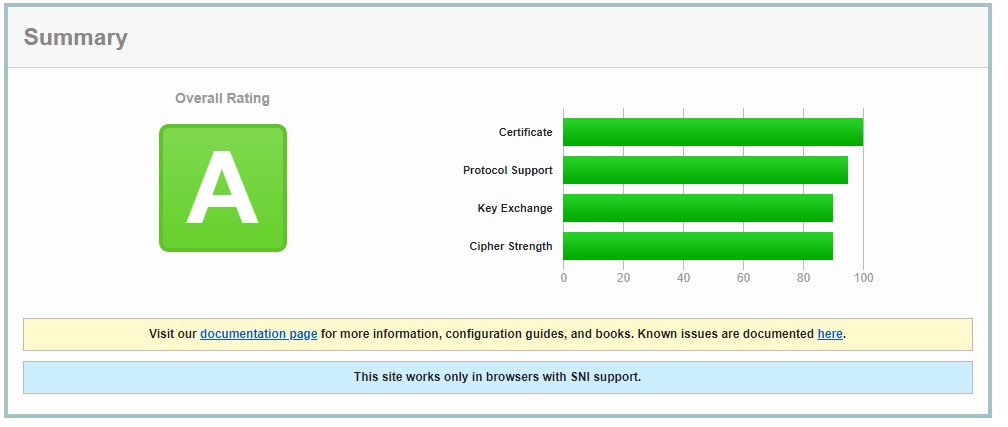
Проверка сертификата
После установки сертификата certbot предложит проверить ssl для указанного домена на их сайте:
https://www.ssllabs.com/ssltest/analyze.html?d=domain.com
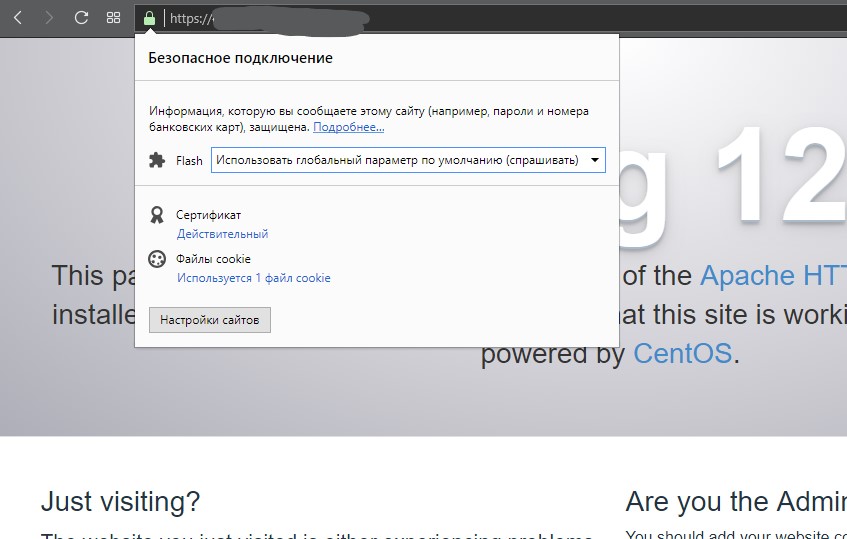
Можно сделать проще — открываем сайт в браузере https://example.com
Настройка автоматического продления сертификата
|
1 |
vi /etc/crontab |
|
1 |
30 2 * * * root certbot renew >> /var/log/le-renew.log |